For years, AI assistants have been reactive & waiting for our prompts. The Frontier Agents flip the script. Now, they are proactive, persistent and most importantly, specialized.
At AWS re:Invent 2025, the global annual conference hosted by Amazon Web Services, the company unveiled their new groundbreaking agentic AI system called "AWS Security Agent".
What is AWS Security Agent?
AWS Security Agent is an AI-powered autonomous security analyst that proactively secures your applications throughout the development lifecycle across all your environments and conducts automated security reviews customized to your requirements - without human intervention.
Think of it as having a 24/7 security expert who:
Monitors all your AWS services
Investigates threats when detected
Takes action to stop attacks
Learns from every incident
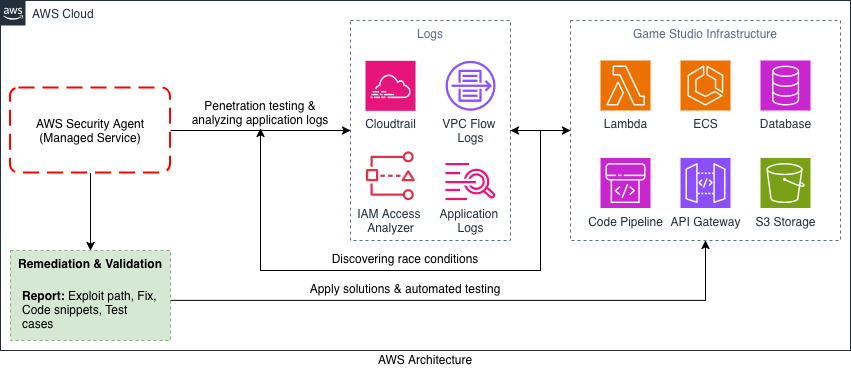
This agent is not just limited to scanning code. It comprehends the application's architecture, its data flows and the specific AWS services it employs. It then tailors its penetration testing and vulnerability scans accordingly. Organizations establish their security standards once, and the agent automatically validates them across applications during reviews.
What's wrong with the Traditional ways of implementing security?
Conventional security implementation tools such as SAST/DAST are essential, but they're infamously noisy. They're designed on a "detect-and-alert" strategy which generates thousands of disjointed alerts daily, most of which are false positives, leading to critical alert fatigue and burnout. This manual process creates dangerous delays and by the time an analyst manually logs in, investigates, and takes action, attackers have already had hours or even days of unimpeded access.
How can AWS Security Agent help?
The AWS Security Agent directly combats the core weaknesses of traditional security by shifting from "detect-and-alert" to "detect-investigate-remediate." Instead of adding to the noise, it acts as an autonomous analyst that consumes alerts, filters the false positives, and automatically takes verified, pre-approved actions to contain threats in minutes. Think of it as a force multiplier for your security team. It handles the repetitive, time-consuming work of triaging thousands of AWS GuardDuty, Security Hub, and Config alerts. The agent correlates these signals, investigates by checking CloudTrail logs, IAM policies, and network flows, and then executes precise responses - like isolating a compromised EC2 instance, applying an IAM deny policy, or rotating exposed credentials - often before a human even logs in.
Let's take an example:
Picture this, A leading game studio is set to release their next generation game featuring expansive world, numerous maps, player-driven economics, real money trading & live competitive events. The attack surface isn't just a game server, it's a complex web of microservices handling player inventories, marketplace transactions, anti-cheat logic and global matchmaking. A security breach in this environment could mean mass theft of digital assets, manipulated leaderboards, or a complete shutdown during a major championship event.
This is where the AWS Security Agent transitions from being merely a compliance tool to a vital competitive safeguard. As the studio prepares to launch this new game, the Security Agent goes beyond conducting a regular vulnerability scan.
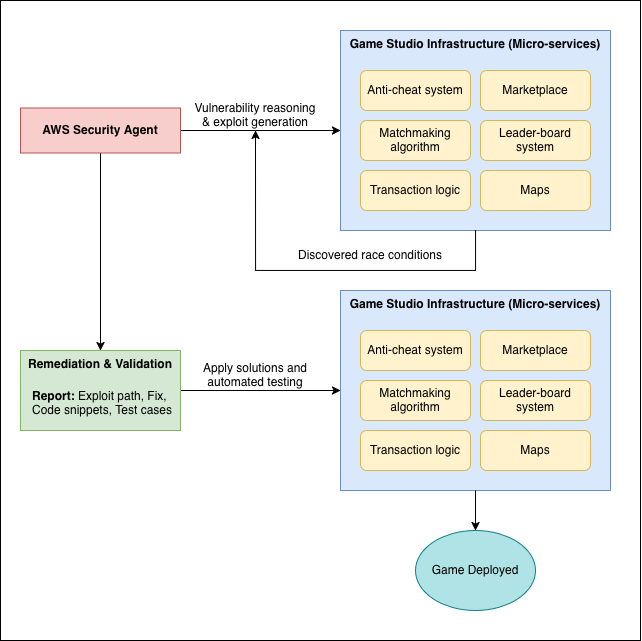
It delves into the game's framework, transaction logic, and competitive dynamics to identify what would be most significant to potential attackers. Equipped with this contextual insight, the Security Agent independently executes game-specific penetration testing throughout the entire launch build - simulating the actions of a malicious player.
During this process, it uncovers a critical race condition buried deep in the game's asset-transfer workflow. Traditional security tools would likely overlook this issue because the vulnerability is not a known signature or a simple misconfiguration. It emerges only when the game's economic rules, transaction timing, and player behavior intersect - something the Security Agent can reason about because it understands the system's intent, not just its surface.
Rather than generating a generic vulnerability report, the AWS Security Agent delivers:
The exact exploit path
The conditions required to trigger it
A recommended code-level fix aligned with the existing architecture
The Security Agent then maps these recommendations directly to the affected code paths and infrastructure components. It highlights the specific services involved, the functions that must be updated, and the tests that should be added to prevent regression. In many cases, it can generate example code snippets or patch-ready guidance that fits seamlessly into the studio's development workflow.
Finally, the agent validates the fix by re-running the same game-specific penetration scenario that exposed the issue in the first place. This closed-loop approach ensures the vulnerability is not just mitigated in theory but eliminated in practice - before the game ever goes live.
Advantages of Security Agent:
Understands Context: It understands how your application is designed to work, where it runs, and what matters most to the business.
Proactive and not Reactive: The AWS Security Agent actively looks for ways a system could be exploited, running customized penetration tests before attackers ever get a chance.
Works continuously: The agent operates autonomously for days at a time, monitoring, testing, and validating security controls without constant human input.
Built for Modern Systems: The AWS Security Agent is designed for Microservices and cloud-native environments, continuously validating security across services, pipelines, and runtime workloads.
Security becomes a competitive advantage: By catching issues early, reducing downtime risk, and protecting user trust, the AWS Security Agent turns security from a bottleneck into an enabler.
Security That Reduces Human Load, Not Adds to It
By combining detection, root-cause analysis, guided remediation, and verification, the AWS Security Agent dramatically reduces the cognitive load on development and security teams during high-pressure launch cycles. Instead of scrambling to interpret vague vulnerability reports, teams receive precise, actionable intelligence that allows them to fix critical issues quickly and confidently.


